话说Spring Security权限管理(源码详解)
发布于 2017-11-25 12:25:28 | 194 次阅读 | 评论: 0 | 来源: 网友投递
Spring Framework 开源j2ee框架
Spring是什么呢?首先它是一个开源的项目,而且目前非常活跃;它是一个基于IOC和AOP的构架多层j2ee系统的框架,但它不强迫你必须在每一层 中必须使用Spring,因为它模块化的很好,允许你根据自己的需要选择使用它的某一个模块;它实现了很优雅的MVC,对不同的数据访问技术提供了统一的接口,采用IOC使得可以很容易的实现bean的装配,提供了简洁的AOP并据此实现Transcation Managment,等等
本篇文章主要介绍了话说Spring Security权限管理(源码详解) ,小编觉得挺不错的,现在分享给大家,也给大家做个参考。一起跟随小编过来看看吧
最近项目需要用到Spring Security的权限控制,故花了点时间简单的去看了一下其权限控制相关的源码(版本为4.2)。
AccessDecisionManager
spring security是通过AccessDecisionManager进行授权管理的,先来张官方图镇楼。
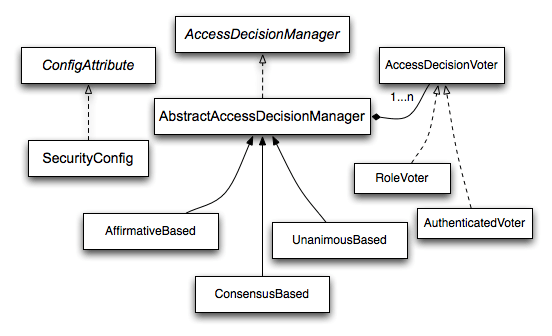
AccessDecisionManager
AccessDecisionManager 接口定义了如下方法:
//调用AccessDecisionVoter进行投票(关键方法)
void decide(Authentication authentication, Object object,
Collection<ConfigAttribute> configAttributes) throws AccessDeniedException,
InsufficientAuthenticationException;
boolean supports(ConfigAttribute attribute);
boolean supports(Class clazz);
接下来看看它的实现类的具体实现:
AffirmativeBased
public void decide(Authentication authentication, Object object,
Collection<ConfigAttribute> configAttributes) throws AccessDeniedException {
int deny = 0;
for (AccessDecisionVoter voter : getDecisionVoters()) {
//调用AccessDecisionVoter进行vote(我们姑且称之为投票吧),后面再看vote的源码。
int result = voter.vote(authentication, object, configAttributes);
if (logger.isDebugEnabled()) {
logger.debug("Voter: " + voter + ", returned: " + result);
}
switch (result) {
case AccessDecisionVoter.ACCESS_GRANTED://值为1
//只要有voter投票为ACCESS_GRANTED,则通过
return;
case AccessDecisionVoter.ACCESS_DENIED://值为-1
deny++;
break;
default:
break;
}
}
if (deny > 0) {
//如果有两个及以上AccessDecisionVoter(姑且称之为投票者吧)都投ACCESS_DENIED,则直接就不通过了
throw new AccessDeniedException(messages.getMessage(
"AbstractAccessDecisionManager.accessDenied", "Access is denied"));
}
// To get this far, every AccessDecisionVoter abstained
checkAllowIfAllAbstainDecisions();
}
通过以上代码可直接看到AffirmativeBased的策略:
- 只要有投通过(ACCESS_GRANTED)票,则直接判为通过。
- 如果没有投通过票且反对(ACCESS_DENIED)票在两个及其以上的,则直接判为不通过。
UnanimousBased
public void decide(Authentication authentication, Object object,
Collection<ConfigAttribute> attributes) throws AccessDeniedException {
int grant = 0;
int abstain = 0;
List<ConfigAttribute> singleAttributeList = new ArrayList<ConfigAttribute>(1);
singleAttributeList.add(null);
for (ConfigAttribute attribute : attributes) {
singleAttributeList.set(0, attribute);
for (AccessDecisionVoter voter : getDecisionVoters()) {
//配置的投票者进行投票
int result = voter.vote(authentication, object, singleAttributeList);
if (logger.isDebugEnabled()) {
logger.debug("Voter: " + voter + ", returned: " + result);
}
switch (result) {
case AccessDecisionVoter.ACCESS_GRANTED:
grant++;
break;
case AccessDecisionVoter.ACCESS_DENIED:
//只要有投票者投反对票就立马判为无权访问
throw new AccessDeniedException(messages.getMessage(
"AbstractAccessDecisionManager.accessDenied",
"Access is denied"));
default:
abstain++;
break;
}
}
}
// To get this far, there were no deny votes
if (grant > 0) {
//如果没反对票且有通过票,那么就判为通过
return;
}
// To get this far, every AccessDecisionVoter abstained
checkAllowIfAllAbstainDecisions();
}
由此可见UnanimousBased的策略:
- 无论多少投票者投了多少通过(ACCESS_GRANTED)票,只要有反对票(ACCESS_DENIED),那都判为不通过。
- 如果没有反对票且有投票者投了通过票,那么就判为通过。
ConsensusBased
public void decide(Authentication authentication, Object object,
Collection<ConfigAttribute> configAttributes) throws AccessDeniedException {
int grant = 0;
int deny = 0;
int abstain = 0;
for (AccessDecisionVoter voter : getDecisionVoters()) {
//配置的投票者进行投票
int result = voter.vote(authentication, object, configAttributes);
if (logger.isDebugEnabled()) {
logger.debug("Voter: " + voter + ", returned: " + result);
}
switch (result) {
case AccessDecisionVoter.ACCESS_GRANTED:
grant++;
break;
case AccessDecisionVoter.ACCESS_DENIED:
deny++;
break;
default:
abstain++;
break;
}
}
if (grant > deny) {
//通过的票数大于反对的票数则判为通过
return;
}
if (deny > grant) {
//通过的票数小于反对的票数则判为不通过
throw new AccessDeniedException(messages.getMessage(
"AbstractAccessDecisionManager.accessDenied", "Access is denied"));
}
if ((grant == deny) && (grant != 0)) {
//this.allowIfEqualGrantedDeniedDecisions默认为true
//通过的票数和反对的票数相等,则可根据配置allowIfEqualGrantedDeniedDecisions进行判断是否通过
if (this.allowIfEqualGrantedDeniedDecisions) {
return;
}
else {
throw new AccessDeniedException(messages.getMessage(
"AbstractAccessDecisionManager.accessDenied", "Access is denied"));
}
}
// To get this far, every AccessDecisionVoter abstained
checkAllowIfAllAbstainDecisions();
}
由此可见,ConsensusBased的策略:
- 通过的票数大于反对的票数则判为通过。
- 通过的票数小于反对的票数则判为不通过。
- 通过的票数和反对的票数相等,则可根据配置allowIfEqualGrantedDeniedDecisions(默认为true)进行判断是否通过。
到此,应该明白AffirmativeBased、UnanimousBased、ConsensusBased三者的区别了吧,spring security默认使用的是AffirmativeBased, 如果有需要,可配置为其它两个,也可自己去实现。
投票者
以上AccessDecisionManager的实现类都只是对权限(投票)进行管理(策略的实现),具体投票(vote)的逻辑是通过调用AccessDecisionVoter的子类(投票者)的vote方法实现的。spring security默认注册了RoleVoter和AuthenticatedVoter两个投票者。下面来看看其源码。
AccessDecisionManager
boolean supports(ConfigAttribute attribute);
boolean supports(Class<?> clazz);
//核心方法,此方法由上面介绍的的AccessDecisionManager调用,子类实现此方法进行投票。
int vote(Authentication authentication, S object,
Collection<ConfigAttribute> attributes);RoleVoter
private String rolePrefix = "ROLE_";
//只处理ROLE_开头的(可通过配置rolePrefix的值进行改变)
public boolean supports(ConfigAttribute attribute) {
if ((attribute.getAttribute() != null)
&& attribute.getAttribute().startsWith(getRolePrefix())) {
return true;
}
else {
return false;
}
}
public int vote(Authentication authentication, Object object,
Collection<ConfigAttribute> attributes) {
if(authentication == null) {
//用户没通过认证,则投反对票
return ACCESS_DENIED;
}
int result = ACCESS_ABSTAIN;
//获取用户实际的权限
Collection<? extends GrantedAuthority> authorities = extractAuthorities(authentication);
for (ConfigAttribute attribute : attributes) {
if (this.supports(attribute)) {
result = ACCESS_DENIED;
// Attempt to find a matching granted authority
for (GrantedAuthority authority : authorities) {
if (attribute.getAttribute().equals(authority.getAuthority())) {
//权限匹配则投通过票
return ACCESS_GRANTED;
}
}
}
}
//如果处理过,但没投通过票,则为反对票,如果没处理过,那么视为弃权(ACCESS_ABSTAIN)。
return result;
}
很简单吧,同时,我们还可以通过实现AccessDecisionManager来扩展自己的voter。但是,要实现这个,我们还必须得弄清楚attributes这个参数是从哪儿来的,这个是个很关键的参数啊。通过一张官方图能很清晰的看出这个问题来:
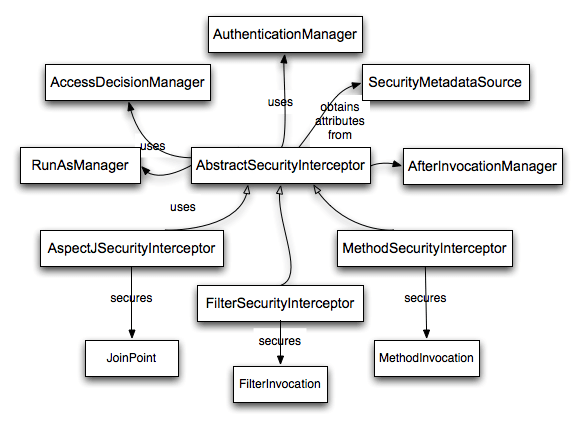
接下来,就看看AccessDecisionManager的调用者AbstractSecurityInterceptor。
AbstractSecurityInterceptor
...
//上面说过默认是AffirmativeBased,可配置
private AccessDecisionManager accessDecisionManager;
...
protected InterceptorStatusToken beforeInvocation(Object object) {
...
//抽象方法,子类实现,但由此也可看出ConfigAttribute是由SecurityMetadataSource(实际上,默认是DefaultFilterInvocationSecurityMetadataSource)获取。
Collection<ConfigAttribute> attributes = this.obtainSecurityMetadataSource()
.getAttributes(object);
...
//获取当前认证过的用户信息
Authentication authenticated = authenticateIfRequired();
try {
//调用AccessDecisionManager
this.accessDecisionManager.decide(authenticated, object, attributes);
}
catch (AccessDeniedException accessDeniedException) {
publishEvent(new AuthorizationFailureEvent(object, attributes, authenticated,
accessDeniedException));
throw accessDeniedException;
}
...
}
public abstract SecurityMetadataSource obtainSecurityMetadataSource();
以上方法都是由AbstractSecurityInterceptor的子类(默认是FilterSecurityInterceptor)调用,那就再看看吧:
FilterSecurityInterceptor
...
//SecurityMetadataSource的实现类,由此可见,可通过外部配置。这也说明我们可以通过自定义SecurityMetadataSource的实现类来扩展出自己实际需要的ConfigAttribute
private FilterInvocationSecurityMetadataSource securityMetadataSource;
...
//入口
public void doFilter(ServletRequest request, ServletResponse response,
FilterChain chain) throws IOException, ServletException {
FilterInvocation fi = new FilterInvocation(request, response, chain);
//关键方法
invoke(fi);
}
public void invoke(FilterInvocation fi) throws IOException, ServletException {
if ((fi.getRequest() != null)
&& (fi.getRequest().getAttribute(FILTER_APPLIED) != null)
&& observeOncePerRequest) {
// filter already applied to this request and user wants us to observe
// once-per-request handling, so don't re-do security checking
fi.getChain().doFilter(fi.getRequest(), fi.getResponse());
}
else {
// first time this request being called, so perform security checking
if (fi.getRequest() != null) {
fi.getRequest().setAttribute(FILTER_APPLIED, Boolean.TRUE);
}
//在这儿调用了父类(AbstractSecurityInterceptor)的方法, 也就调用了accessDecisionManager
InterceptorStatusToken token = super.beforeInvocation(fi);
try {
fi.getChain().doFilter(fi.getRequest(), fi.getResponse());
}
finally {
super.finallyInvocation(token);
}
//完了再执行(父类的方法),一前一后,AOP无处不在啊
super.afterInvocation(token, null);
}
}
好啦,到此应该对于Spring Security的权限管理比较清楚了。看完这个,不知你是否能扩展出一套适合自己需求的权限需求来呢,如果还不太清楚,那也没关系,下篇就实战一下,根据它来开发一套自己的权限体系。
以上就是本文的全部内容,希望对大家的学习有所帮助,也希望大家多多支持PHPERZ。